Tuesday, 13 August 2013
Sunday, 11 August 2013
Zorin OS 6.2 lite has been Released
Zorin OS Lite 6.2 is built on the Linux architecture so it is completely open source and it's based on Ubuntu, one of the most used Linux operating system in the world.
This latest version of Zorin OS Lite is still based on Lubuntu 12.04.2 (Precise Pangolin), which was released only a couple of days ago, and it uses the LXDE desktop environment.
Zorin Look Changer, Zorin Internet Browser Manager, Zorin OS Lite Extra Software and other programs from earlier versions have been added to Zorin OS 6.2 Lite.
Download (MD5) from here: zorin-os-6.2-lite.iso (650MB)
Another Great Ubuntu Flavor Linux Lite 1.0.6 (Based on Ubuntu 12.04)
It is also recommended to those people who are new to Linux or for those who want really lightweight desktop environment. It is also great choice for old laptop or desktop you gave up on a few years back. Linux Lite is a showcase for just how easy it can be to use Linux. From familiar software like Firefox and Thunderbird, to simply named menu items, to one click updates and software installs.
Linux Lite team just released 1.0.6 version for 32bit and 64bit with Xfce desktop environment, based on Ubuntu 12.04.
Linux Lite 1.0.6 new features include easier networking setup between Linux Lite and Windows or other Linux operating systems, a system report tool to help troubleshoot problems, support for scanners, Bluetooth and a brand-new login screen. The Help and Support Manual is our most comprehensive to date and is available both offline and online.
Changelog:
- Firefox 21.0
- Kernel 3.2.0.40 pae
- Rewrote Help & Support Manual
- Added Scanner support.
- Added Bluetooth.
- Added 'Drives' shortcut to home folder.
- Added Show Desktop button.
- Added support for iDevices.
- Added right click 'Open as Administrator' to Thunar.
- Added/Removed Install Additional Software scripts.
- Added Enable/Disable automatic login to System menu.
- Added Network Share Settings to System menu.
- Added Create System Report to System menu.
- Replaced Wicd with Network Manager.
- New live boot menu.
- New login screen.
- New install slides.
- Announcement of the Linux Lite Shop.
- Fixed auto login if chosen during installation.
- Bug fixes.
- and So on...
Screenshots
Boot Screen
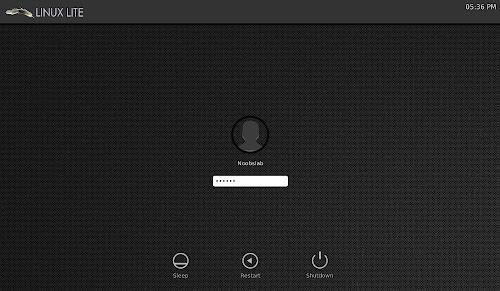
Login Screen
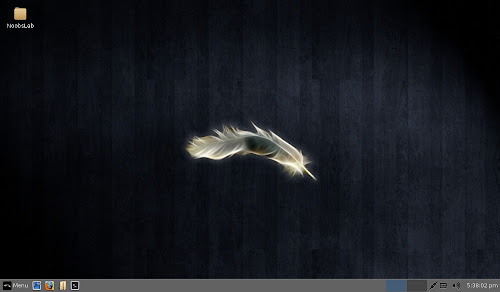
Desktop
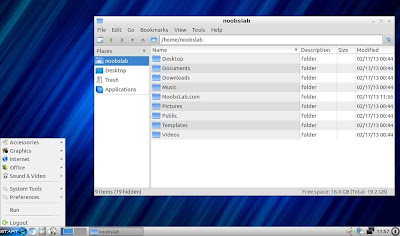
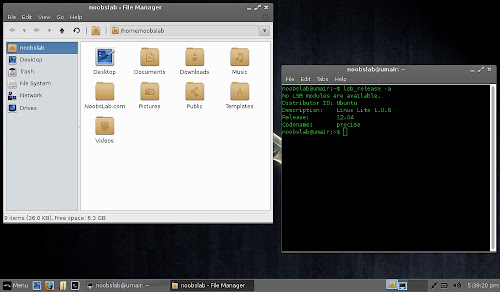
File Manager & Terminal
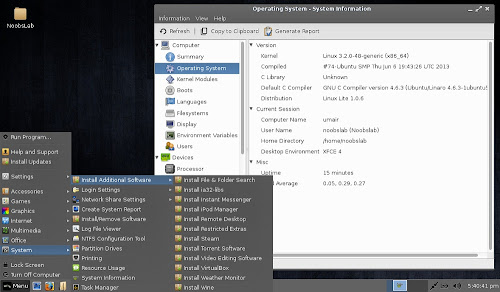
Additional Software & System Info Tool
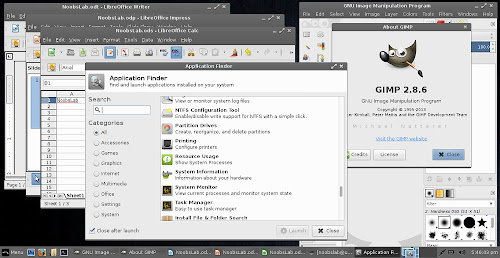
Installed Applications & Application finder
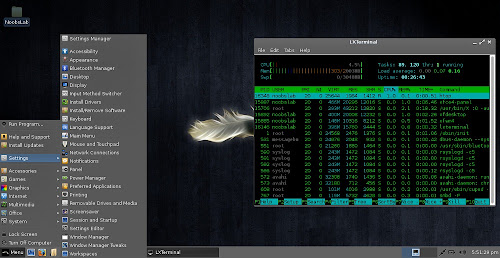
Task Manager
Yahoo Messenger is one of the highly
popular and most widely used instant messaging service in the world
offering a wide variety of features to its users, all for free. This has
made it the right choice for all those who are waiting to chat and
communicate with their far away friends and relatives.
However, while some people use Yahoo
Messenger only to chat with their friends and known ones, many others
use it to have fun by joining the chat rooms and chatting with the
strangers. If you’re a similar person who would like to have fun during
the chat, this post if for you!
In this post, I will show you some really interesting Yahoo Messenger hacks
using which it is possible to play pranks with your friends and
strangers during the chat. Below is a list of some cool hacks that
you’re sure to enjoy:
1. Chat with Multiple Names Simultaneously
How about chatting with your friend with
two or more different names at a time? Well, do not think that this is
impossible! This can easily be done with a simple workaround which
enables you to chat with as many different names as you can with the
same or different people.
For example, you may chat with Person-A using one name and with Person-B
using the other. You can also chat with the same person using different
names or any other combination. All of this goes really unnoticed by
the user on the other side, while you are sure to have some real fun.
Here is a step-by-step procedure to implement this hack:
-
Sign in to your Yahoo Messenger. From the top, click on Messenger -> My Account Info. You will be taken to a web page where you need to log in to your account.
-
Now, you should be on the Profile Settings page. Scroll down to see the option Account Settings as shown below. From there, click on the link which says: “Manage your Yahoo! aliases”.

-
From the Aliases page, click on: “Add an alias”. You can create as many aliases you want. Choose unique names for your alias and once you’re done, click on “close”.
- You need to sign out of Yahoo Messenger and sign in
again to see the changes. Once you have done this, double-click on any
name from your contact list or chat room to open a new chat window. You
should now see a list of your aliases appearing in the chat window to
choose from.

-
To chat with multiple names with a single person, just follow the steps below:
-
Double-click on the name of the person in the chat room or contact list.
-
Select any name from your “alias” list and ping the user with that name. Immediately close the chat window before you get a reply from that person.
-
Again double-click on the same person’s name and ping him/her with another name from your “alias” list. This time do not close the window.
-
Just wait a few seconds! When the person replies to both your pings, you will have two tabs in the same chat window from where you can chat with the same person using two different names. Enjoy!!!
-
How to Know if Someone Accessed My Computer When I am Away
Do you have a feeling that someone tried to access your computer
when you stepped out for a lunch or quick coffee break? Perhaps
your colleague or the person sitting in the next desk tried to log in or
play something wicked on your computer while you were away for a quick
session.
So, how do you know if someone tried to
access your computer in your absence? Well, here is a way by which you
get notified every time when such an attempt is made.

The website called MouseLock.co
gives a solution here. All you have to do is visit the site’s homepage,
sign in to your Gmail account and select your secret point (unlock
code) from the screen. Once you do this, you will have to place your
mouse cursor into the slot shown and click on it. This will activate the
mouse lock feature on your computer screen.

So, when an unauthorized person tries to
move the mouse in your absence, he will be given just a few seconds to
select the unlock code. Upon failure to do so, you will get an instant
notification about the intrusion in your mailbox.

If you have a webcam attached to your
computer, you can even get the photo of the person trying to intrude.
This will make it easy for you to figure out who actually was the
person.
As this is an easy to use web
application, you can use it any time just by loading the MouseLock
website without the need to install anything on your computer. Even
though MouseLock does not manage to prevent the intrusion, it will give
you an instant notification about it, so that you aware of what is
happening at your desk when you are away.
How it Works?
MouseLock operates by using the
“mouseLeaveEvent” from JQuery to track the mouse movements. On the other
hand, it uses the “getUserMedia()” API that is supported by Chrome and
Firefox to capture the webcam photographs.
Subscribe to:
Posts (Atom)